🚀 𝗘𝘅𝗽𝗹𝗼𝗿𝗲 𝘁𝗵𝗲 𝗶𝗺𝗽𝗼𝗿𝘁𝗮𝗻𝗰𝗲 𝗼𝗳 𝘀𝘆𝘀𝘁𝗲𝗺 𝗺𝗼𝗻𝗶𝘁𝗼𝗿𝗶𝗻𝗴!
🔍 Discover why it's more than just a practice—it's a crucial reminder for users to stay vigilant. 💼🔒 Uncover the truth and fortify your defenses!
#SystemSecurity #StayVigilant 🏢

De domeinnaam systemsecurity.eu is vanaf nu te koop voor 70,00 EUR. #systemsecurity #koopdomeinnaam koopdomeinnaam.nl/systemsecurity…

Stay ahead of cyber threats with ExtremeVPN's proactive patch management solutions. Keep your systems secure and up-to-date with timely software updates.
#PatchManagement #CyberSecurity #ExtremeVPN #SoftwareUpdates #SystemSecurity #StayProtected #DigitalSecurity #TechSecurity



The Official (ISC)2 CISSP CBK Reference by Arthur J. Deane (Author) Wiley (Publisher) Buy from computer bookshop using this link: tinyurl.com/2jkwfmb9 #systemsecurity #cissp #softwaredevelopment #networksecurity #softwareengineering #securityengineering #books


Relax on #longweekend & let ISO 27001 take care of your systems & keep #cybersecuriy #threats at bay!
Contact #Anitech for #ISO27001 & #ISMS services-1300 802 163 or e-mail – [email protected]
#systemsecurity #ISMS services #ISO27001 implementation #ISO27001 certification


Activate your payout authentication is against unauthorized access.
By activating this layer of security, you're ensuring that only trusted users have the power to make payouts, keeping your assets and information locked away from prying eyes
#MarasoftPay #SystemSecurity


Unlock the future of cybersecurity with Senteon! From automated checks to proactive threat prevention, ensure your systems stay one step ahead. 🚀
#cybersecurity #continuousmonitoring #complianceassurance #senteon #threatprevention #systemsecurity


Is your #cloud security built on sandcastles or #Fort Knox? Don't let your #data evaporate! #NetworkFort builds #unbreachable #Cyberwalls around your #cloud empire #CloudSecurity #DataFortress #DontBeCloudy
Get a FREE #cloud #securityaudit
#web3 #aisecurity #system security #system



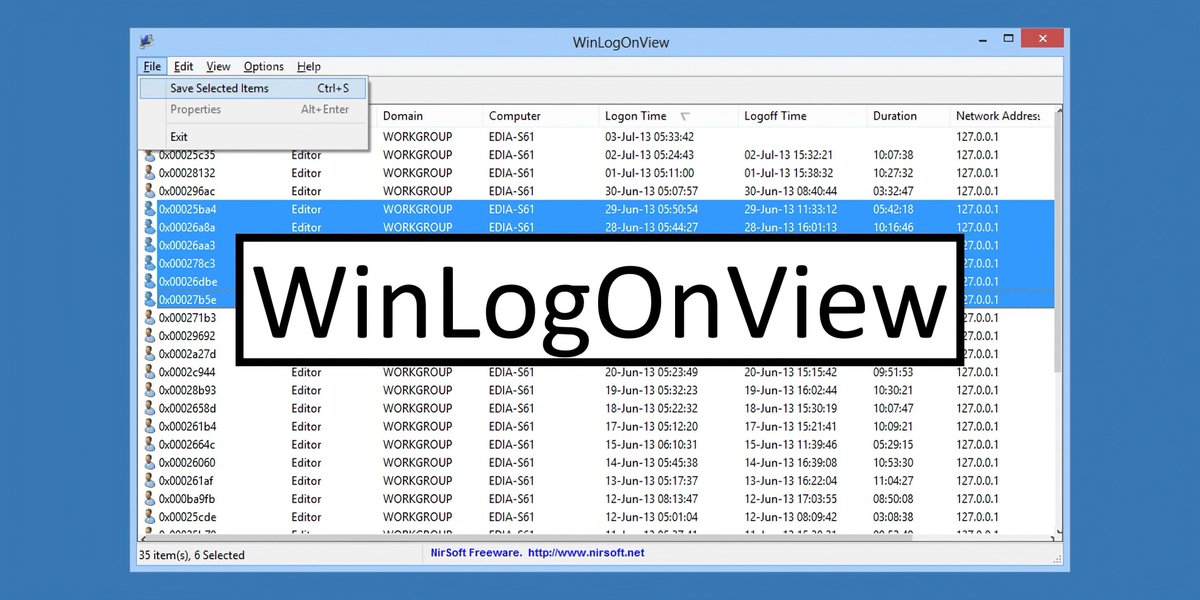
🔍 WinLogOnView is a handy tool that searches the event log to provide a detailed report on the logins and logouts of credentials on your Windows machine. 👤💻 Stay on top of your system's activities with this useful software! #WindowsTips #WinLogOnView #SystemSecurity


The security of your systems is your first line of defense. ♟️🛡️
Read our blog to discover the role of DISA STIGS in ensuring systems are set up and configured securely. ⬇️
#CyberDefense #SystemSecurity #CyberSecurity
ow.ly/rKvx50R7uJt

🚀 Experience the cutting-edge expertise of 12 Futuretech, where we offer a comprehensive web development service package to transform your online presence. ! 💻🌐 #12Futuretech #WebDevelopment #UIUXDesign #FrontEndDevelopment #HostingAndDomain #BackEndDevelopment #SystemSecurity



#IEMLabs #securityframework #cybersecurity #cybersecurity awareness #cybersecurity training #cybersecurity tips #systemsecurity


Unveiling the Essential Responsibilities of a Linux Sysadmin: From Command Line Mastery to System Security and Scripting Savvy.
Read more: networkworld.com/article/130658…
#LinuxSysadmin #SystemAdministration #CommandLine #SystemSecurity #Scripting #TechSkills #ITInfrastructure