




Demostración de cómo podemos programar un script de Python para realizar fuzzing web, de tal forma que veremos la aplicación de Python en la ciberseguridad. #hackingetico #python #python programming #python ciberseguridad #ciberseguridadpython #scripting

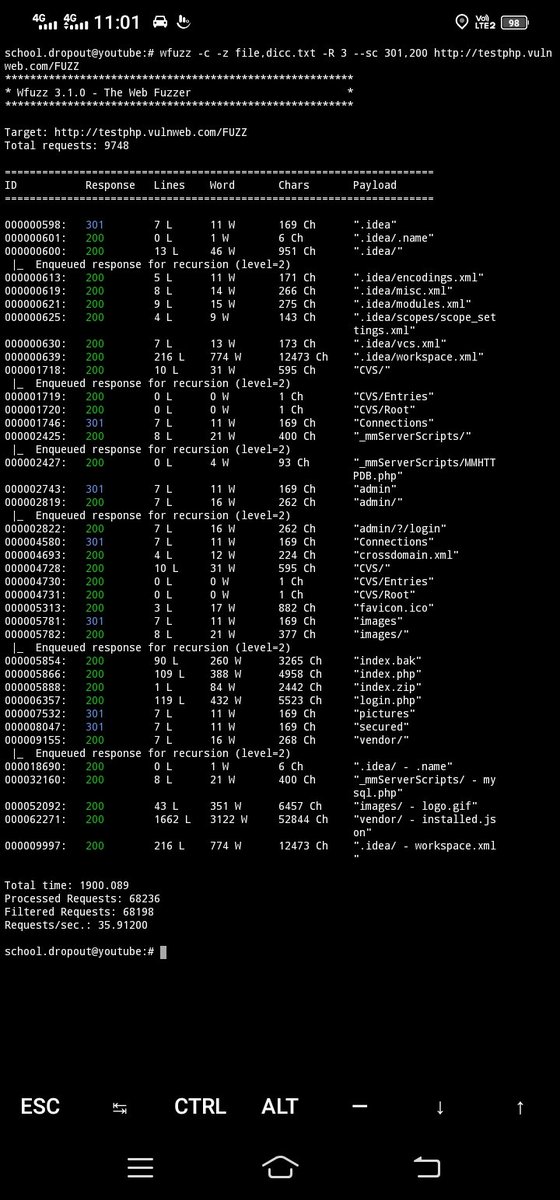
🔎 Recursive Fuzzing with WFUZZ 💻
wfuzz -c -z file,wordlist -R 3 --sc 301,200 target/FUZZ
#bugbounty tips #bugbounty

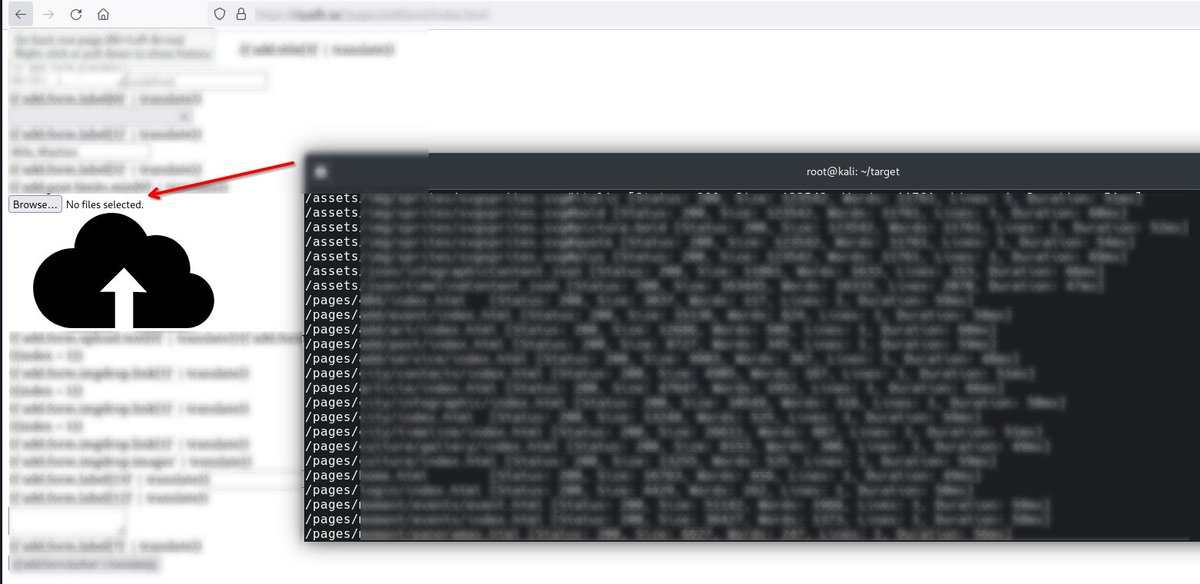
When You Recon for Old Urls, and there is to much output you Can use , cut or awk to print only found paths then export them as a fuzzing wordlist .txt and test them , found me a file upload :)
#bugbountytips



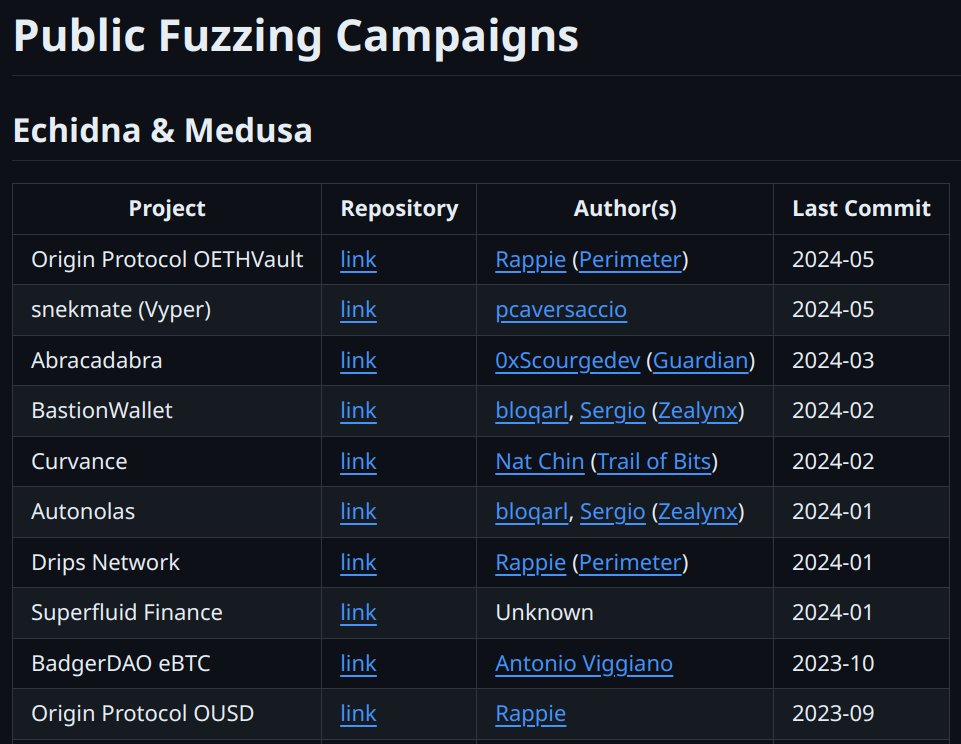
Some new additions to the Public Fuzzing Campaigns List:
- Origin Protocol OETHVault by Rappie (@perimeter_sec)
- snekmate by sudo rm -rf --no-preserve-root /
- Autonolas by bloqarl and Sergio (@ZealynxSecurity)
- Bastion Wallet by bloqarl and Sergio…

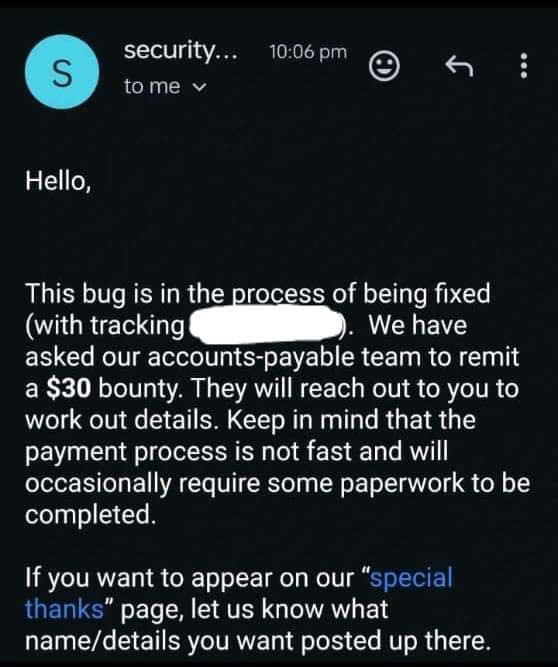
#CyCatz #cybersecurity An easy bounty using fuzzing
More... shorturl.at/CW029
#cyberawareness #cyberattack #breaches #darkwebmonitoring #SurfaceWebMonitoring #mobilesecurity #emailsecurity #vendorriskmanagement #BrandMonitoring #security #information #bugbounty #fuzzing
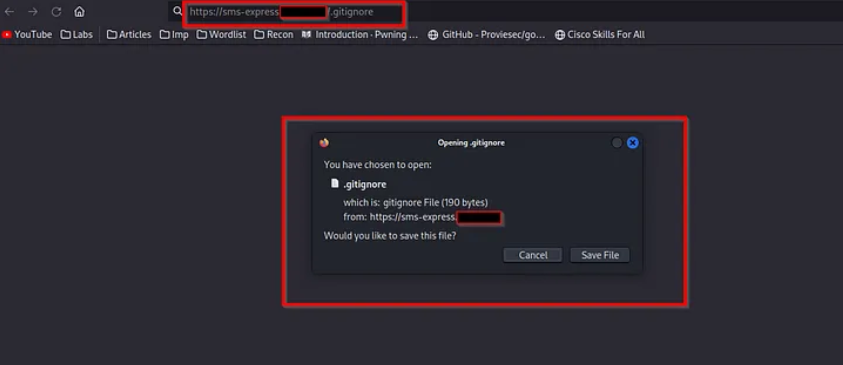




when I test on one of my private targets on h1 I found this site that have an service for administrators of the site but I try some techniques after some fuzzing I found this endpoint /admin/index.html with a white page
Can us help me Godfather Orwa 🇯🇴 🇸🇦 ROOD | GOAT


If you liked Bill Demirkapi @ Offensive Con’s great talk on Secure Boot at offensivecon (new remote write vuln over HTTP boot - my fuzzing students will notice that glaring Content-Length bug) be sure to check out the two prior research releases from my team at Eclypsium!


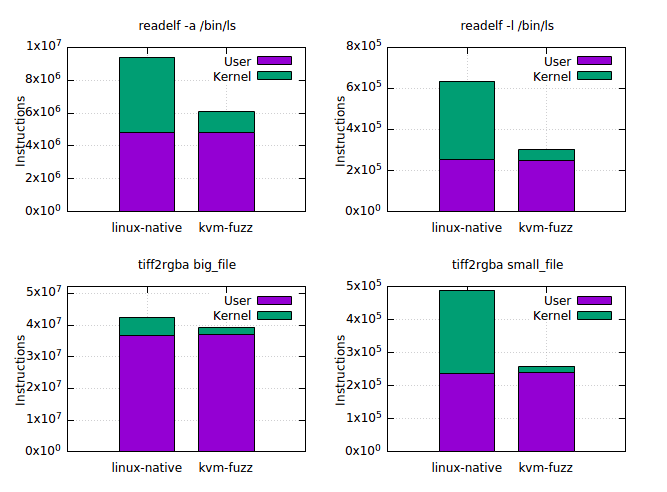
PoC of fuzzing closed-source userspace binaries with KVM github.com/klecko/kvm-fuzz #Pentesting #CyberSecurity #fuzzing #Infosec



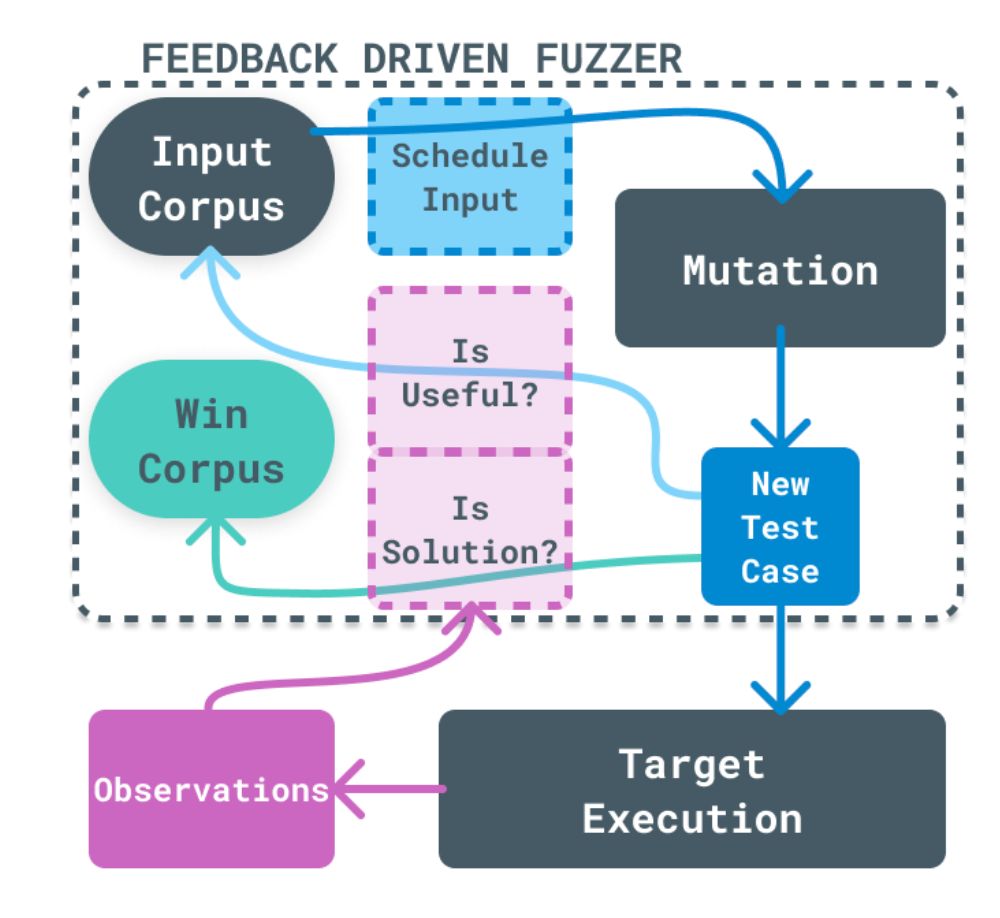
![FuzzingLabs (@FuzzingLabs) on Twitter photo 2024-05-07 15:11:06 📡 [Monthly Fuzzing] May 2024
Here is the latest fuzzing news released last month!
📺 Videos/Podcasts
- Discoveries from Analyzing 141 Real-World ZK-SNARK Vulnerabilities! 🧐 - youtu.be/oxvcEXha69c
📝 Blogposts/Papers/Slides
- ImageIO, the infamous iOS Zero Click Attack… 📡 [Monthly Fuzzing] May 2024
Here is the latest fuzzing news released last month!
📺 Videos/Podcasts
- Discoveries from Analyzing 141 Real-World ZK-SNARK Vulnerabilities! 🧐 - youtu.be/oxvcEXha69c
📝 Blogposts/Papers/Slides
- ImageIO, the infamous iOS Zero Click Attack…](https://pbs.twimg.com/media/GM_CjnlXMAAJmBn.jpg)