Your business is susceptible to disasters like hardware failure, human error, software failure, or natural disaster. Make sure you’re protected with CMIT Solutions: bit.ly/2F1ck1D
#business #computersecurity #networksecurity



BleepinComputer: Example email being sent to site owners and online store admins.
BleepingComputer received the following this week: twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork
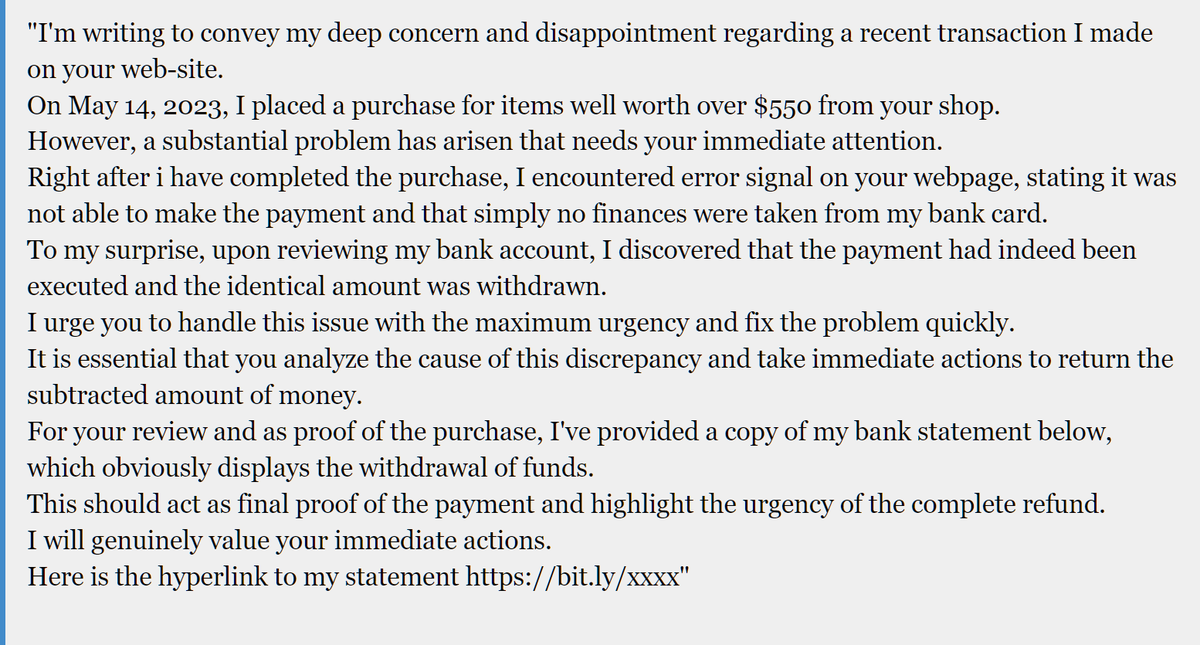



Online sellers targeted by new information-stealing malware campaign - Lawrence Abrams
bleepingcomputer.com/news/security/…

BleepinComputer: Online sellers targeted by new information-stealing malware campaign - Lawrence Abrams
bleepingcomputer.com/news/security/… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork

Get protection from intrusive ads, trackers, and malware. bit.ly/43FegSY
#cybersecurity #computersecurity #privacy #privacy protection #VPN #virtualprivatenetwork

BleepinComputer: Windows 11 to require SMB signing to prevent NTLM relay attacks - Sergiu Gatlan
bleepingcomputer.com/news/security/… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork

3 Benefits of Data Protection Services
#datascience #dataanalyst #datarecovery #remoteaccess #itsupport #cloudservices#cloudstorage #networksecurity#database #datarecovery services #cybersecuritytraining #computersecurity #datadestruction



BleepinComputer: Malicious Chrome extensions with 75M installs removed from Web Store - Bill Toulas
bleepingcomputer.com/news/security/… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork


BleepinComputer: Burton Snowboards discloses data breach after February attack - Sergiu Gatlan
bleepingcomputer.com/news/security/… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork

BleepinComputer: Learn how to make your own ChatGPT bots with this $30 bundle
bleepingcomputer.com/offer/deals/le… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork

BleepinComputer: NSA and FBI: Kimsuky hackers pose as journalists to steal intel - Bill Toulas
bleepingcomputer.com/news/security/… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork

BleepinComputer: Write more efficiently with this Scrivener 3 deal
bleepingcomputer.com/offer/deals/wr… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork

Your business is susceptible to disasters like hardware failure, human error, software failure, or natural disaster. Make sure you’re protected with CMIT Solutions: bit.ly/2F1ck1D
#business #computersecurity #networksecurity


NSA and FBI: Kimsuky hackers pose as journalists to steal intel - Bill Toulas
bleepingcomputer.com/news/security/…

Burton Snowboards discloses data breach after February attack - Sergiu Gatlan
bleepingcomputer.com/news/security/…


👏 Spruce is hiring a remote Software Engineer, Mobile #Spruce #remotework #remotejob #workfromhome #Android #IOS #Rust #SDK #CICD #BluetoothLowEnergy #WiFi #ComputerSecurity himalayas.app/companies/spru…

Shield yourself against sneaky computer viruses with our premier computer services.
#ComputerSecurity #VirusProtection #TopRankedServices #GadgetFix #VirusRemoval #MalwareRemoval #ComputerVirus #malware #ticktocktech #TikTok #iPhone #Netflix


Malicious Chrome extensions with 75M installs removed from Web Store - Bill Toulas
bleepingcomputer.com/news/security/…


The average cost of downtime after a ransomware attack is a staggering $126,000, including lost revenue. With cybercriminals bypassing traditional defenses, it's crucial to ask: Are you truly protected? #cybercrime #cabalaconsolidated #computersecurity 🛡️💻🔒


Your business is susceptible to disasters like hardware failure, human error, software failure, or natural disaster. Make sure you’re protected with CMIT Solutions: bit.ly/2F1ck1D
#business #computersecurity #networksecurity


Windows 11 to require SMB signing to prevent NTLM relay attacks - Sergiu Gatlan
bleepingcomputer.com/news/security/…

Zyxel shares tips to protect firewalls from ongoing attacks - Bill Toulas
bleepingcomputer.com/news/security/…

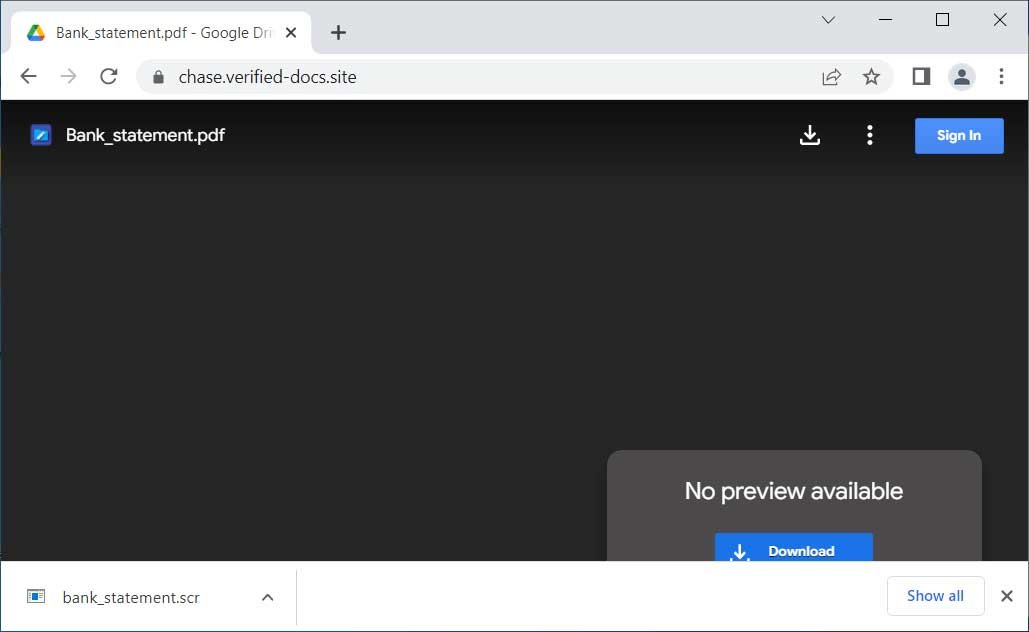
BleepinComputer: When downloading the file, the fake Google Drive site will push a bank_statement.scr file that is detected as Vidar by Triage.
tria.ge/230602-15z3asf… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork



BleepinComputer: Zyxel shares tips to protect firewalls from ongoing attacks - Bill Toulas
bleepingcomputer.com/news/security/… twitter.com/BleepinCompute… #cybersecurity #hacking #computersecurity #nyc #newyork