
Exciting update from #QNAP ! We're boosting our product security through a partnership with Zero Day Initiative ( #ZDI ). Fresh from our participation in Pwn2Own Toronto 2023, we're advancing data protection for users worldwide. 🌍💻 #Cybersecurity #DataProtection #TechInnovation



SPECIAL EDITION NEWSLETTER JUST DROPPED👇👇
Pwn2Own Winner Manfred Paul agreed to answer a handful of questions for this weeks newsletter
Check it out here 🏴☠️
blog.exploits.club/exploits-club-…
Regular recaps and job postings resuming next week

In a new guest blog, Cody Gallagher describes the bug he used to exploit #Oracle #VirtualBox at #Pwn2Own Vancouver. He gives an in-depth analysis of how he used a race condition to win $20,000 at the contest.
zerodayinitiative.com/blog/2024/5/9/…

CVE-2024-2887: A Pwn2own Winning Bug In Google Chrome zerodayinitiative.com/blog/2024/5/2/… #Pentesting #CVE #Pwn2own #BugBounty #WebSecurity #Infosec
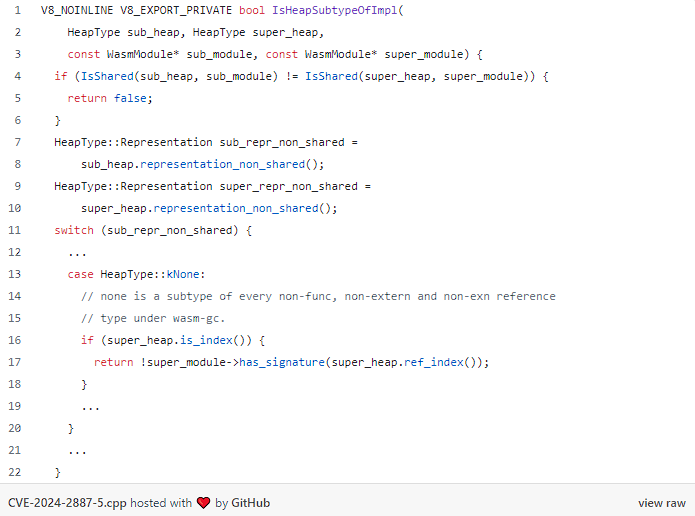


In this guest blog from Master of Pwn winner Manfred Paul, he details CVE-2024-2887 - a type of confusion bug that occurs in both Google Chrome and Microsoft Edge (Chromium).
Learn more from Trend Micro's Zero Day Initiative: bit.ly/44u0J2b


QR5 Cyber Special Guest - Dustin Childs (Pwn2Own/Trend Micro) Zero Day Initiative - Vancouver 2024! #cyber #cyber security #pwn2own The Dustin Childs #ic3games USCyberGames Emu Exploit Manfred Paul x.com/i/broadcasts/1…

In a new guest blog, #Pwn2Own winner Manfred Paul details CVE-2024-2887 - a bug he used to exploit both #Chrome and #Edge during the contest on his way to winning Master of Pwn. He breaks down the root cause and shows how he exploited it. Read the details at zerodayinitiative.com/blog/2024/5/2/…


🔥 Breaking down CVE-2024-2887: Discover the Pwn2Own winning bug in Google Chrome! Dive into the technical details and implications of this vulnerability. #CyberSecurity #InfoSec #GoogleChrome bit.ly/4biRzYU


[ZDI-24-418|CVE-2024-4405] (Pwn2Own) Xiaomi Pro 13 mimarket manual-upgrade Cross-Site Scripting Remote Code Execution Vulnerability (CVSS 8.8; Credit: Nguyen Xuan Hoang, vudq16, Nguyễn Đình Biển, Q5Ca from VCSLab) zerodayinitiative.com/advisories/ZDI…





