
Browse through this all #encompassing guide defining how SMBs can save with managed IT solutions to learn and leverage the benefits for your business, too.
codeepsilon.com/cost-efficienc…
#itcompany #digitalmarketing #itconsulting #networksecurity #wedoit #itsecurity #laptop #jcchelp


#OnTheBlog
Ransomware… A Cyberthreat That Will Keep You Up At Night
Read the full story here:
jcchelp.com/ransomware-a-c…
#JCCHelp #ITSolutions #ITProject #ITServices #MSP #Cybersecurity #Cybersecurity RiskAssessment #databreaches #dataprivacy #datasecurity #ransomware


Troubleshoot POS machines. Ran a new set of cabling, reloaded software, reconnected cabling to switch and tested with the manager.
#JCCHelp #ITSupport #ITProject #networksystem #internet #connectivity #troubleshooting #POS #cablinginstallation #software #networkswitch


#DidYouKnow
65% of ransomware infections are delivered via phishing
Contact us to learn more!
#cybersecurity #cyberattacks
#CybersecurityRiskAssessment #cyberstrategy #dataprivacy #dataprotection #databreaches #datasecurity #phishing #cyberthreats


Jackson Computer Consulting, LLC Hi, dear. We are a specialized factory of PoE modules, which are the same as pin to pin AG9700 AG9600 AG9400,AG5324.AG5312AG5305.AG5405AG9800MAG9900M/AG9900MTAG9900LP...


#OnTheBlog
Data Phishing Awareness
Read the full story here:
jcchelp.com/data-phishing-…
#JCCHelp #ManagedServicesProvider #MSP #Cybersecurity #Cybersecurity RiskAssessment #databreaches #dataprivacy #datasecurity #phishing #phishing awareness #phishing attacks #dataphishing


Installed a total of 13 Polycom IP phones. Hooked all new phones to existing cabling. Plugged in new phones to computers and tested.
#JCCHelp #ITSupport #ITProject #ITproblems #networksystem #internet #connectivity #installation #IPphones #Polycom #phonesystem #businessphones


#OnTheBlog
Beware of Phishing… Get to know their tricks!
Read the full story here:
jcchelp.com/beware-of-phis…
#JCCHelp #MSP #Cybersecurity #Cybersecurity RiskAssessment #databreaches #dataprivacy #datasecurity #phishing #phishing awareness #phishing attacks


Installed 2 new security cameras inside this office's production area. Adjusted the angle for full scope and tested with the manager.
#JCCHelp #ITSupport #ITProject #networksystem #internet #connectivity #installation #securitycameras #CCTV #indoorcamera


Installed a Fortigate switch and router. The site contact tested them and its online. Connected 7 access points to it and tested connectivity.
#JCCHelp #ITSupport #ITProject #networksystem #internet #connectivity #installation #Fortigate #switch #router #accesspoints #AP


Troubleshoot FIOS connectivity issue. Checked the internet connection, tested cabling. Found out that the issue is within the switches inside.
#JCCHelp #lowvoltagetechnician #pghtech #networksystem #internet #connectivity #troubleshooting #cablingissue #FIOS #switch


#WhatYouNeedToKnow
Learn about the 2 most common threats to cybersecurity:
1. Malware - Applications or links that
install malicious software
2. Phishing - Attackers pretending to be
a genuine entity
#cybersecurity #cyberattacks #databreaches #datasecurity #malware #phishing


⚡ Unleash Innovation at NECA #NECASHOW2023 ! ⚡
📅 Sep 30 - Oct 2, 2023 📍 Philadelphia
Connect with experts, and explore cutting-edge tech! 🛠️
Featuring: Aida Corporation Directional Systems Jackson Computer Consulting, LLC
Don't miss out – secure your spot now! 🎉
Follow us for updates. 🚀


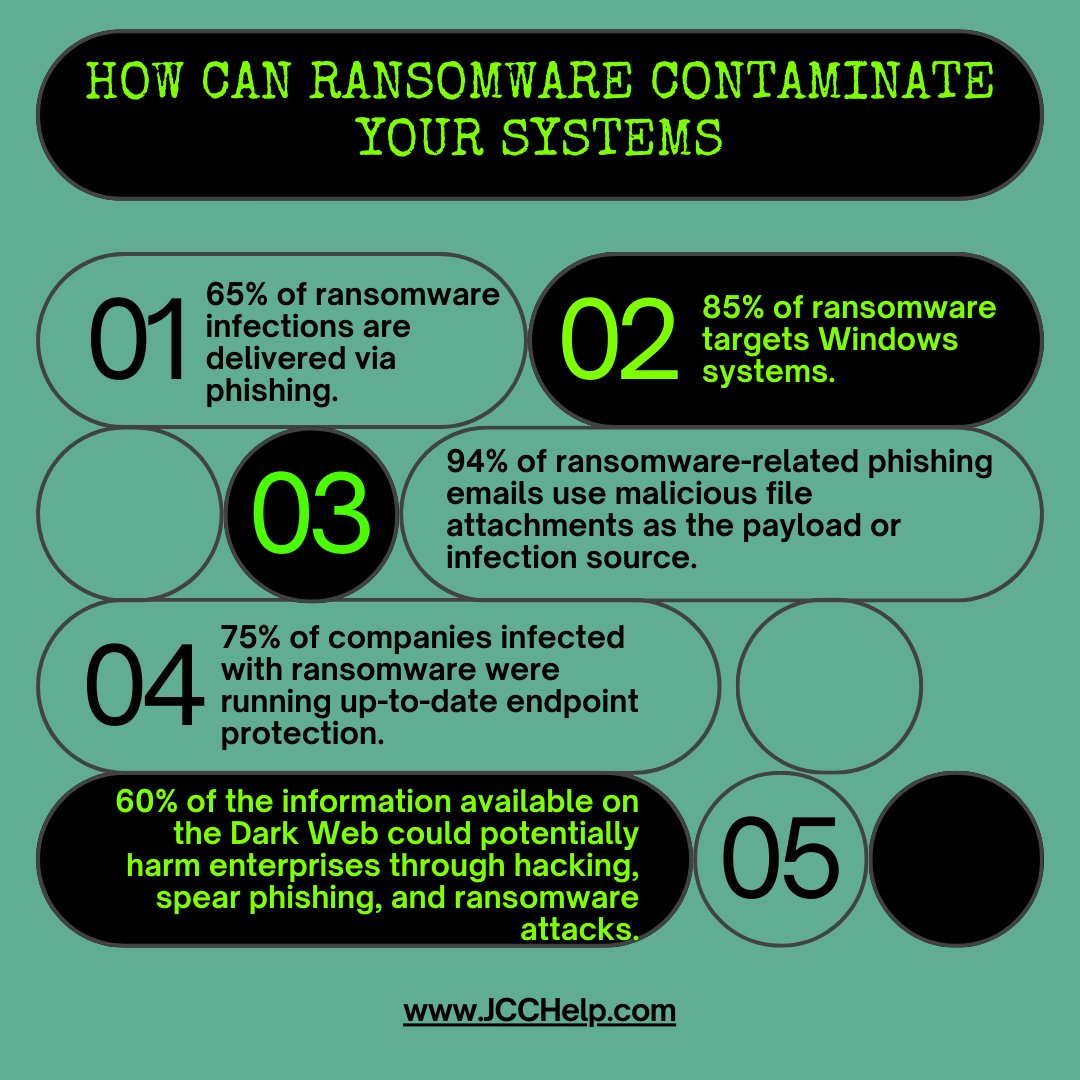
#TechTips
How can ransomware contaminate your systems?
To defend against ransomware, you need to understand where it comes from, how it reaches you, and how it infects your systems.
#ITServices #MSP #tipsandtricks #cybersecurity #cyberattacks #cyberthreats #ransomware

#InTheNews
THREAT ACTORS HACKED THE DROPBOX SIGN PRODUCTION ENVIRONMENT
Source: tinyurl.com/24f58va9
#ITNews #NewsToday #databreach es #datasecurity #dataprivacy #DropboxSign #cybersecurity #infosec #databreach #hacking

#InTheNews
Kaiser notifies 13.4M individuals of data breach
Source: healthitsecurity.com/news/kaiser-no…
#ITNews #NewsToday #infosec #databreaches #datasecurity #dataprivacy #Kaiser #healthservices #Kaiser FoundationHealthPlan

Jackson Computer Consulting, LLC Incident response is not something to be overlooked.
If you have a lot of assets, it is important to map everything out and define adequate response for each threats they are facing.
You will also define roles and responsibilities.
Preparation is key 🔑

Jackson Computer Consulting, LLC Jackson Computer Consulting, LLC I can't decide. They're all pros. 💯