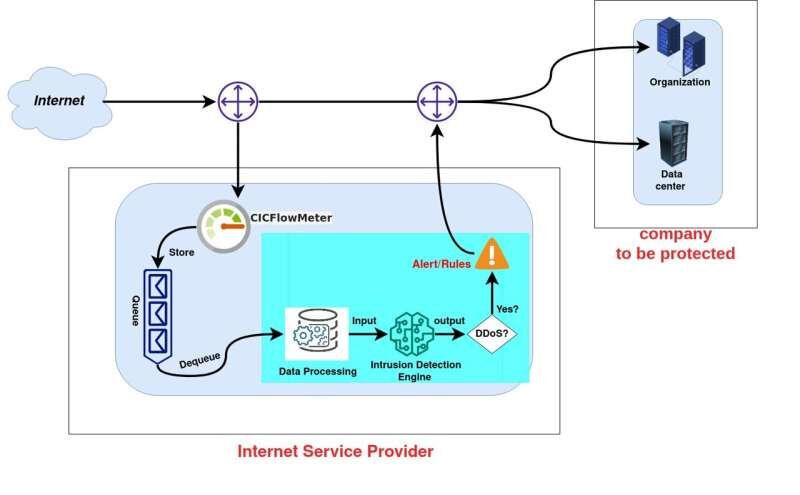
Don't let those DDoS attacks ruin your day - take action to protect your online business today!
lectron.com/say-goodbye-to…
#DDoSProtection #OnlineSecurity #CyberProtection #DDoSAttacks #WebsiteSecurity #CyberAttacks #MitigationTools #OnlineBusinessSecurity
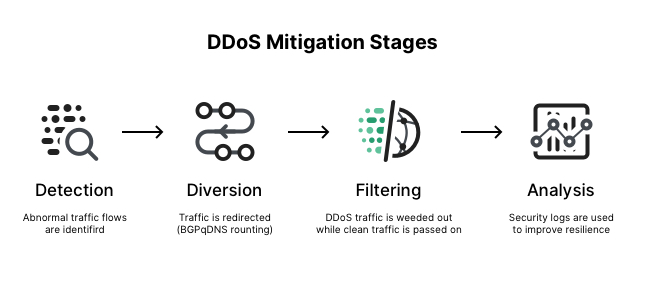

Fight DDoS attacks on every front! 👾🛡️ Gcore protects your network across L3, L4, & L7 layers for full-scale protection.
Ready to secure the integrity of your network? ➡️ gcore.cc/3JmUh3A
#ddosprotection #ddosattacks #cybersecurity #websecurity #cloudsecurity

As technology advances, the prevalence of online threats increases. Get acquainted with different types of cyber attacks your devices 💻 📲 can fall prey to, resulting in the loss of sensitive data.
#cyberattacks #onlinethreats #malware #mitm #ddosattacks #phishing #bruteforce


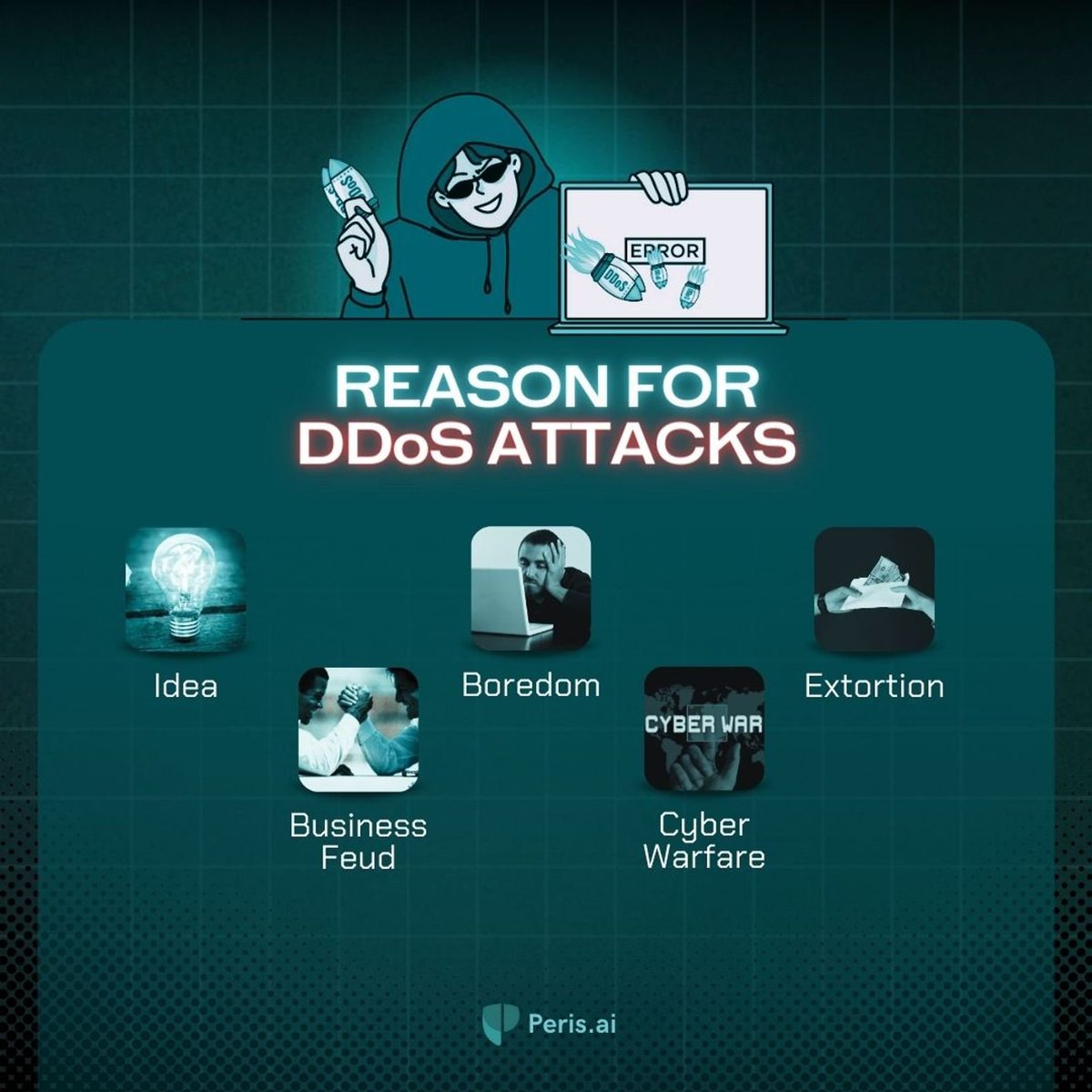
Understanding the Reasons Behind DDoS Attacks.
#DDoSAttacks #ITSecurity #ThreatDetection #InformationSecurity #DataProtection #DigitalSecurity #CyberWarfare #StaySafeOnline #Perisai #Cybersecurity #YouBuild #WeGuard

Demystifying DDoS Attacks: Understanding the Various Types with SpaceProtect! From volumetric to application layer attacks, SpaceProtect provides insights into the different types of DDoS attacks and how to defend against them. Stay informed, stay protected! #DDoSAttacks


1 day 1 DDoS fact :
Day 4 -
Did you know? DDoS attacks are often used as a smokescreen to divert attention while other malicious activities, like data theft or network infiltration, take place. Stay alert to multi-layered threats.
#DDoSAttacks #Cybersecurity #DDoSProtection …


DDoS attacks can cripple your online ops. 💥 But our mitigation strategies are your virtual shield, deflecting malicious traffic and keeping you resilient. Stay vigilant, and stay online with our expert guidance! #DDoSAttacks #DDoSMitigation #CyberSecurity #RealizePossibilities …


#ddos #waap #firewall #applicationsecurity #cybersecurity #ddos attacks #ddos mitigation #ddos protection #ddos solutions #apptrana #indusface
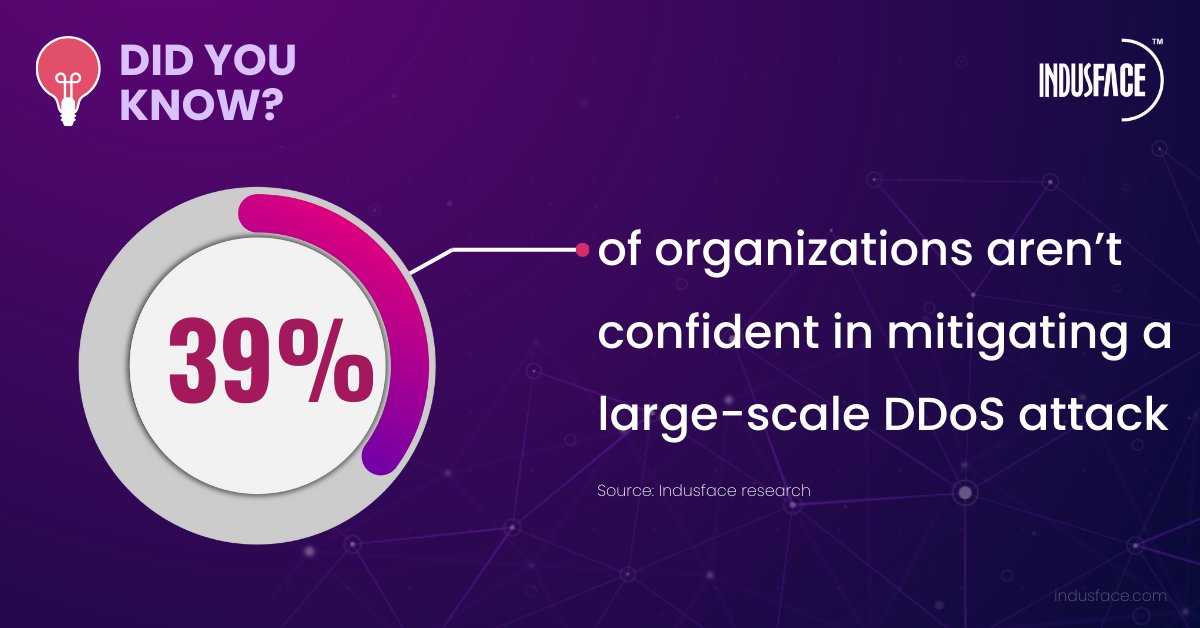


According to Cloudflare , there was a spike in #DDoS attacks after #Hamas ’ #October7 attack on Israel ישראל 🇮🇱
#CyberSecurity #ransomware #software #supplychain attacks #DDoS attacks #malware #engineered #phishing attempts

Cybercriminals have devised sophisticated methods to exploit security vulnerabilities in IoT devices to launch DDoS attacks on businesses.
Learn how to combat DDoS attacks with AI. buff.ly/3Jlkij7
#DDoSattacks #IoTsecurity #ai #edgesecurity #security #cybersecurity


Get fortified with Gcore's XDP/eBPF expertise! Our cutting-edge techniques ensure quick, uninterrupted updates for ultimate #CyberResilience 🛡️
More insights on The New Stack➡️ gcore.cc/3QvDSxq
#ddosprotection #ddosattacks #CyberSecurity

Partner with us to protect your business network, domains, and systems from a #DDoS cyber-attack!
With Liquid you will have higher visibility of potential attacks, automatically mitigate threats and proactively secure your business.
#DDosSecure #DDoS Attacks #CyberSecurity

The pro-Russian hacker group #Noname057 (16) has launched DDoS attacks on energy companies based in #Germany and #Sweden - RWE & Vatenfall - citing political conflict related to the Russia-Ukraine war. #cybersecurity #ddosattacks
Stay vigilant!


Mr.Dempsey hackers group claims to target and attack UAE infrastructures.
#UAE
#cti #threatintel #Cyberattack #DDoSAttacks

Enhancing Cybersecurity with Managed IT Solutions bit.ly/3QvIiEL #Cybersecurity #CyberThreat #cyberattack #ThreatDetection #DDoSattacks #databreaches #AttackSolutions


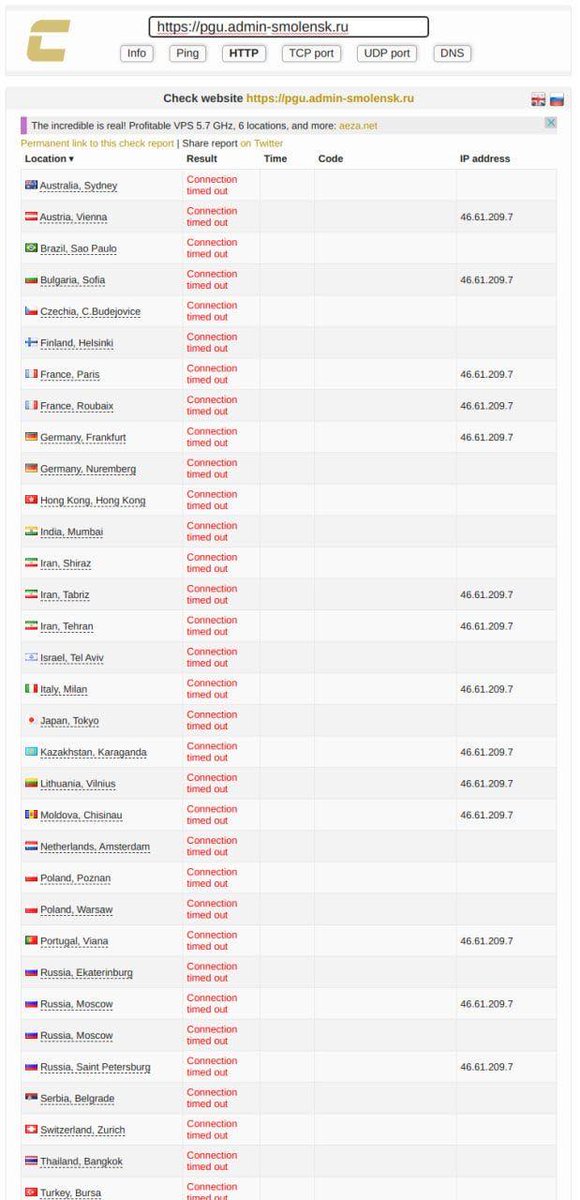
NoName hackers group targeted the website of the Swedish company Kvarken Ports Ltd, uniting the ports of Umeå and Vaasa.
Note: Website is down at the moment.
#Sweden #cti #threatintel #cyberattack #ddosattacks

Explore the vibrant online realm where websites thrive. Beware #DDoSattacks . Unlock #security with Prophaze. Ready to elevate your digital presence? Join the future of #CyberProtection : hubs.la/Q01-PxLc0
#OnlineSecurity #DigitalFortress #StaySafeOnline

🔍 Dive into our latest article, featuring the 'Top 13 #DDoS Protection Software in the Market for 2024.'
#ddosprotection #ddosmitigation #ddosattacks #ddossolutions #ddosprotection software #cybersecurity #waf #waap #applicationlayer #applicationsecurity #apptrana #indusface