Jonny Johnson
@jsecurity101
Principal Windows Security Researcher @HuntressLabs | Windows Internals & Telemetry Research
ID:746411413074116608
https://linktr.ee/jonny.johnson 24-06-2016 18:35:23
2,1K Tweets
6,9K Followers
378 Following







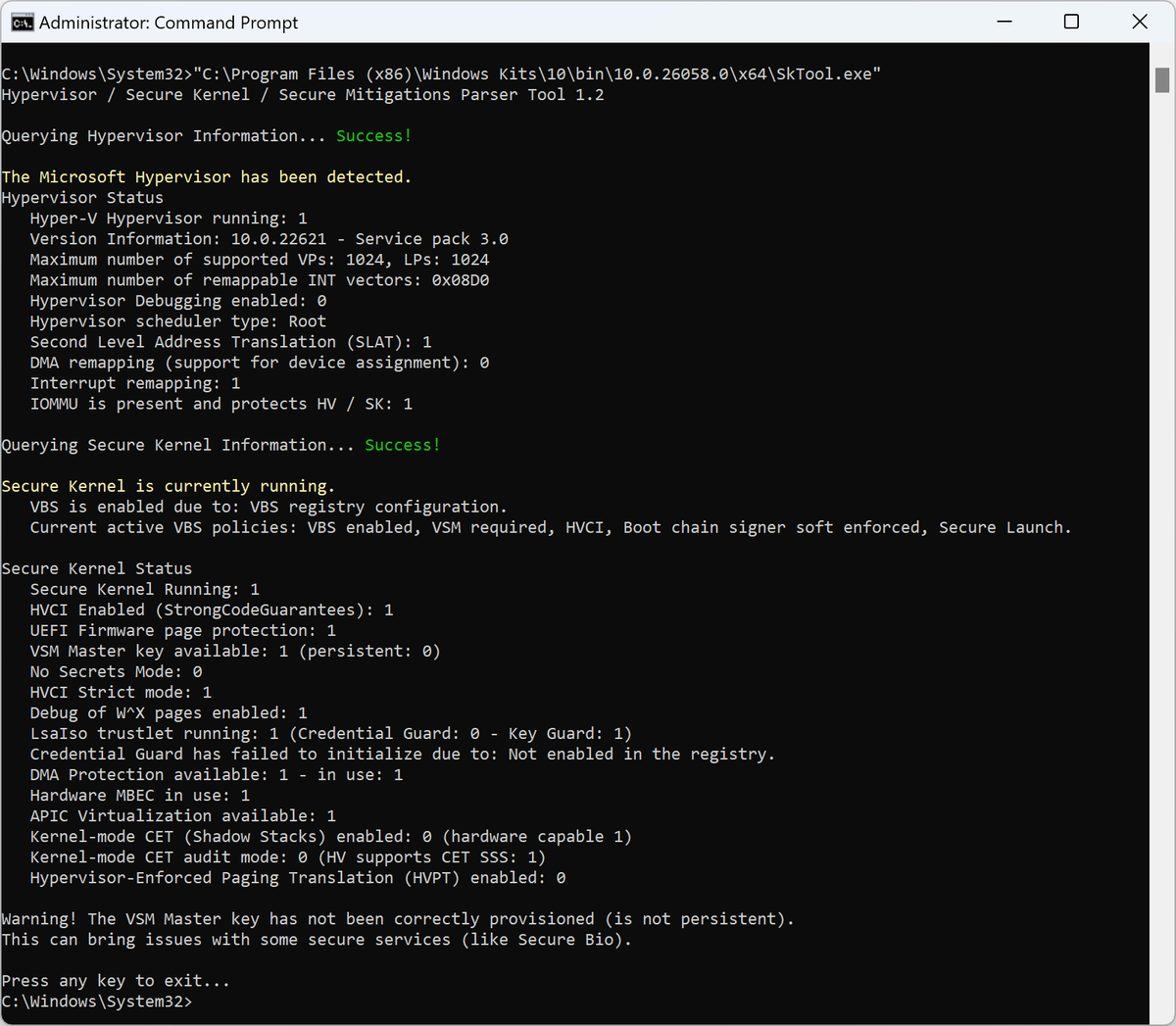
Shout out to Andrea Allievi for building SkTool. The easiest way to find out what Hypervisor / secure kernel features are enabled on a system







Quick poll. Reasoning for answer not need so even quicker with Yes and No. 😄
#cyber security
Do individual contributors in #cyber security have acces to enough time to learn more and improve their #knowledge ?